Get assistance with your schoolwork! Find the answers to hundreds of questions about education (Computer Systems and Applications) in an easy-to-understand format. If you can't find the answer to your issue here, you can always send it to our specialists!
Computer Systems And Applications Past Questions and Likely Examination Questions with Answers.
The System software includes Operating System ( OS ) ,device drivers and other system utility programs . The application software are used by the computer user to perform various tasks on the system. The commonly used application software includes MS Word , Excel .
Computer Systems and Applications Question and Answers.
1. Which of the following has the lowest processing capability?
A. Supercomputer
B. Mainframe
C. Minicomputers
D. Microcomputers
ANSWER: D
2. One of the following is not an operating system
A. Linux
B. IOS
C. Windows
D. Berry Os
ANSWER: D
3. Which of the following is the most appropriate language used in developing an operating system.
A. Machine Language
B. Assembly Language
C. Third Level Language
D. High Level Language
ANSWER: B
4. A double word is a group of
A. 4 bytes
B. 32 bytes
C. 2 bytes
D. 3 bytes
ANSWER: A
5. The Operating system is a/an
A. Systems software
B. Driver
C. Application Software
D. I/O
ANSWER: A
6. Which of the following Registers contains the address of the next instruction
A. AC
B. MAR
C. PC
D. MDR
ANSWER: C
7. A byte is a group of …………………………..
A. 32 bits
B. 8 bits
C. 4 bits
D. 16 bits
ANSWER: B
8. One of the following is not a main function of the OS
A. Memory Management
B. Processor Management
C. Device Management
D. Power Supply Management
ANSWER: D
9. COBOL Programming Language was introduced during the
A. First Generation
B. Second Generation
C. Fourth Generation
D. Third Generation
ANSWER: B
10. One of the following is not an input device.
A. Keyboard
B. Scanner
C. Projector
D. Mouse
ANSWER: C
11. A paragraph is ……………………..
A. 200 Bit
B. 32 bit
C. 128 bit
D. 110 bit
ANSWER: C
12. One of the following in MS Word helps you display the number of pages in your document.
A. View Bar
B. Dialog Box
C. Status Bar
D. Transition Tab
ANSWER: C
13. How many registers are in the CPU
A. Unlimited
B. 5
C. 4
D. 2
ANSWER: B
14. An Avast Antivirus by default operates in the ……………………
A. User Mode
B. I/O Mode
C. Driver Mode
D. Kernel Mode
ANSWER: A
15. 1101 in binary is the same as ……………………
A. E in Hex
B. A in Hex
C. C in Hex
D. D in Hex
ANSWER: D
16. Self-driving car will use …………………..
A. Desktop OS
B. NOS
C. DOS
D. RTOS
ANSWER: D
17. We can only READ from one of the following hardware devices ……………………..
A. RAM
B. Pendrive
C. Hard Disk
D. ROM
ANSWER: D
18. All application programs run in the ……………………..
A. User Mode
B. Kernel Mode
C. Full Mode
D. Partial mode
ANSWER: A
19. Versatility in Computer means …………………………..
A. They have high speed
B. They can perform any task
C. They don’t get tired
D. They have large storage capacity
ANSWER: B
20. Unsigned number systems represent …………………
A. Negative and Positive numbers
B. None of the Above
C. Negative numbers
D. Positive numbers
ANSWER: D
21. IBM 1400 series is an example of a ……………….
A. Second Generation computer
B. Third Generation computer
C. First Generation computer
D. Fourth Generation Computer
ANSWER: A
22. In computer System, the Bank Teller can be likened to: ………
A. RAM
B. Operating System
C. Processor
D. The Kernel
ANSWER: B
23. Which of the following OS will you recommended for an internet café ;
A. Timesharing OS
B. Network OS
C. Distributed OS
D. Desktop OS
ANSWER: B
24. The CPU does not contain one of the following ………….
A. Control Unit
B. PC.
C. ALU
D. Memory
ANSWER: D
25. Which of VLSI Stand for ……………………………………
A. Very Light Scale intelligence
B. Very Large Scale Integrator
C. Very Large Scale Integration
D. None of the Above
ANSWER: C
26. To convert from Decimal to Hex, you will use ………………..
A. Polynomial expansion by 16
B. Successive division by 2
C. Successive division by 16
D. Positional notation by 16
ANSWER: C
27. AND and NOT operations are performed by the ………………….
A. Memory
B. ALU
C. Control Unit
D. Registers
ANSWER: B
28. JAVA is an example of ………………………..
A. An Assembly programming language
B. A middle level programming language
C. A high level programming language
D. A low level programming language
ANSWER: C
29. Magnetic Core Memory is …………………….
A. Semi-Volatile
B. Volatile
C. Fast-Volatile
D. Non-volatile
ANSWER: D
30.Unsigned number systems represent …………………….
A. Positive numbers
B. None of the Above
C. Negative and Positive numbers
D. Negative numbers
ANSWER: A
31. The most commonly used architecture in Ethernet LAN is the
A. Bus Topology
B. Ring Topology
C. Mesh Topology
D. Star topology
ANSWER: D
32. The most powerful component of a client-server network architecture is the
A. Client
B. Server
C. Internet
D. Optical Fibre
ANSWER: B
33. One of the following is not a weakness of a client –server network architecture
A. Central point of failure
B. Can cause network congestion
C. Faster access
D. Server software require
ANSWER: C
34. Switches operate at ……………………………… of the OSI reference model.
A. Application layer
B. Physical layer
C. Session layer
D. Data link layer
ANSWER: D
35. A network that spreads geographically across a country or Globe is the
A. The WAN
B. The MAN
C. The LAN
D. The OSI
ANSWER: A
36. A quadword is a ………………… bit data item
A. 4
B. 32
C. 128
D. 64
ANSWER: D
37. To achieve adding signed binary numbering systems, one must know.
A. Positional Notation
B. Division by 2
C. 2’s Complement
D. Radix System
ANSWER: C
38. E in Hexadecimal is the same as …………………. In Decimal
A. 12
B. 9
C. 15
D. 14
ANSWER: D
39. Unicode Transformation Format uses variable bit encoding for the following bits excepts
A. 64 bits
B. 8 bits
C. 16 bits
D. 32 bits
ANSWER: A
40. Extended ASCII uses ………………………… bits
A. 7 bits
B. 32 bits
C. 8 bits
D. 64 bits
ANSWER: C
41. A double word is made up of ………………….. bytes
A. 2 bytes
B. 32 bytes
C. 1 bytes
D. 4 bytes
ANSWER: D
42. 14 in Decimal converted to Binary will gave you
A. 01112
B. 01012
C. 11102
D. 00102
ANSWER: C
43. Computers understand one of the numbering systems
A. Hexadecimal
B. Decimal
C. Binary
D. Octal
ANSWER: C
44. One of the following is a minor function of the operating system
A. File management
B. Processor Management
C. Device Management
D. Concurrency Control
ANSWER: D
45. Distributed systems provide the following advantages except
A. Communication
B. Sensing Network
C. Reliability
D. Computational Speed
ANSWER: D
46. The type of operating system that is most useful for high degree of reliability is
A. Real Time OS
B. Network OS
C. Distributed OS
D. Optical OS
ANSWER: A
47. Application running in user mode and wants to transit to kernel mode must not delegate one of the following systems APIs
A. Interrupt
B. Operating system
C. System Call
D. Kernel Core
ANSWER: D
48. One of the following classes of computers are normally used by Stock Exchanges as servers
A. Supercomputers
B. Main frame Computers
C. Mini Computers
D. Micro Computers
ANSWER: B
49. In second Generation computers, Assembly language replaced
A. High level language
B. C++ Language
C. Java Language
D. Machine Language
ANSWER: D
59. In which generation of computers did semiconductor memory replaced magnetic core memory
A. First Generation
B. Fourth Generation
C. Third Generation
D. Second Generation
ANSWER: B
60. In the Von Neumann Architecture, the Program Counter is part of the
A. ALU
B. Control Unit
C. Registers
D. Input Devices
ANSWER: C
61. The function of the Memory Data Register (MDR) in a CPU is to
A. Hold the address of the next instruction
B. Contain the current instruction during processing
C. Hold data that is being transferred to or from memory
D. Hold storage for ALU results
ANSWER: C
62. The function of the capacitor in Digital Electronics is to
A. Resist the flow of Current
B. Amplify electronic signals
C. Switch electronic Signals
D. Store electrical energy
ANSWER: D
63. Von Neumann Architecture was first published by John Von Neumann in
A. 1945
B. 1944
C. 1946
D. 1943
ANSWER: A
64. On the Motherboard, the Northbridge with heat sink is also Called the
A. I/O controller Hub
B. Memory Controller
C. DRAM
D. GMCH
ANSWER: B
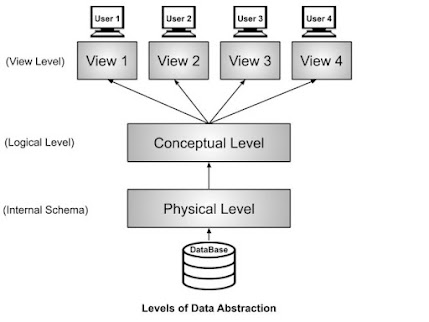
65. The most import component of Data Abstraction is …
A. Physical Schema
B. View
C. Logical Schema
D. ER Diagram
ANSWER: B
66. One of the following is not a type of Object Based Data Model
A. Semantic Data Model
B. Functional Data Model
C. Object Oriented Data Model
D. Frame Memory Model
ANSWER: D
67. One of the following SQL falls under the Data Manipulation Language
A. CREATE
B. ALTER
C. DROP
D. UPDATE
ANSWER: D
68. One of the following is not an advantage of DBMS
A. Data Integrity & Security
B. Data Administration
C. The Software Size is small
D. Efficient Data Access
ANSWER: C
69. All are well known DBMS except
A. Oracle
B. dBase2
C. SAP
D. SQLite
ANSWER: B
70. A Gigabyte is ………………………….. data item
A. 220
B. 230
C. 210
D. 240
ANSWER: B
71. Each hex digit reflects a/an ………………………… sequence
A. 8 bit
B. 16 bit
C. 4 bit
D. 2 bit
ANSWER: C
72. Which type of language is appropriate in writing operating systems and maintaining desktop applications?
A. Machine Language
B. Medium Level Language
C. Java
D. Assembly Language
ANSWER: D
73. In multiprogramming, we have how many CPUs
A. 1
B. 2
C. 5
D. Infinite
ANSWER: A
74. One of the following might not be an Entity in a School Database modelling
A. Student
B. Teacher
C. Student Name
D. Finance
ANSWER: C
75. The property of an Entity in Database modelling is termed
A. Class
B. Attribute
C. Dataset
D. Relationship
ANSWER: B
76. How many schema of Data Abstraction do we have?
A. 3
B. 4
C. 2
D. 5
ANSWER: A
77. The SQL code that helps to remove all records from a table, including all spaces allocated to the record is the
A. DELETE SQL
B. DROP SQL
C. TRUNCATE SQL
D. ALTER SQL
ANSWER: C
78. The network topology that is normally adopted by the Banks is the
A. Tree Topology
B. Mesh Topology
C. Star Topology
D. Ring Topology
ANSWER: B
79. Hub connects segments of a
A. WAN
B. MAN
C. LAN
D. TAN
ANSWER: C
80. Hubs operate at ……………………………….. where data collision is inevitable
A. Half-duplex
B. Quarter-duplex
C. Full-duplex
D. None of the Above
ANSWER: A
81. A router in network in networking normally connects
A. Related networks
B. Orthogonal networks
C. Adjacent networks
D. Different networks
ANSWER: D
82. Routers in networking uses ……………………….. to determine the best for forwarding the packets
A. Only Header Table
B. Only Forwarding Table
C. Header and Lookup Table
D. Header and Forwarding Table
ANSWER: D
83. First Generation Computers were built from
A. 1942-1955
B. 1941-1957
C. 1943 – 1953
D. 1940 – 1960
ANSWER: D
84. One of the following is an example of second Generation Computers
A. UNIVAC
B. IBM 370
C. ENIAC
D. IBM 7094
ANSWER: D
85. The LSI and VLSI were introduced during
A. Fourth Generation Computers
B. First Generation Computers
C. Second Generation Computers
D. Third Generation Computers
ANSWER: A
86. How many registers are well known at the Central Processing Unit
A. 4
B. 3
C. 5
D. 2
ANSWER: C
87. The OSI reference model is a ……………………………. Layer model.
A. 4
B. 6
C. 5
D. 7
ANSWER: D
88. One of the following is not an input device
A. Keyboard
B. Monitor
C. Mouse
D. Joystick
ANSWER: B
89. One of the following is a computer peripheral
A. RAM
B. ROM
C. CPU
D. Printer
ANSWER: D
90. How many levels of data independence do we have.
A. 1
B. 4
C. 3
D. 2
ANSWER: D
91. The ASCII code takes each character on the keyboard and assigns it a / an…
A. Octet number
B. Hex number
C. Binary
D. Decimal number
ANSWER: C
92. Convert 2610 into an 8 bit binary number
A. 000110102
B. 000111112
C. 001111012
D. 101111002
ANSWER: A
93. Convert F in Hex to Binary of 6 bits
A. 0001112
B. 0000112
C. 1100012
D. 0011112
ANSWER: D
94. Convert 1010 to Hexadecimal
A. B
B. 4
C. 5
D. A
ANSWER: D
95. One of the following is not an operating system
A. Linux OS
B. MacOS
C. Windows Vista
D. ZendOS
ANSWER: D
96. The fundamental unit of computer storage is
A. Hex
B. Byte
C. Bit
D. Oct
ANSWER: C
97. The operating systems starts in one of the following modes when it boots
A. Warm boot mode
B. Cold boot mode
C. User Mode
D. Kernel Mode
ANSWER: D
98. One of the following is not an Application software
A. Windows XP
B. Avast Antivirus
C. Microsoft office Suite
D. VLC Media play
ANSWER: A
99. One of the following is an application of Real Time OS
A. Playing audio
B. File Transfer
C. Creating folder
D. Autonomous Vehicle
ANSWER: D
100. Which of the following is known as “Hard booting”
A. Cold boot
B. Fast boot
C. Slow boot
D. Warm boot
ANSWER: A
101. The use of computers to create a 3-D mode of an object is also referred to as …………………….
A. Computer Aided Design (CAD)
B. Computer Aided Manufacturing (CAM)
C. Computer Aided Processing (CAP)
D. Computer Aided Engineering (CAE)
ANSWER: A
102. To connect two similar networks and control their data flow, you need a ………….
A. Bridge
B. Gateway
C. Repeater
D. Router
ANSWER: D
103. What is the term used to arrangement of devices on a network?
A. Protocol
B. Network
C. Topology
D. Interconnection
ANSWER: C
104. What layer of the OSI model allows users to access network services?
A. Application
B. Network
C. Presentation
D. Session
ANSWER: A
105. …………………….. is a form of problem solving often applied to repair failed products and services
A. Safe Mode
B. Troubleshooting
C. Patching
D. Configuring
ANSWER: B
106. The primary of a computer network speed depends on the ……………………
A. Bandwidth
B. Data
C. Network
D. Reception
ANSWER: A
107. A program that tells the operating system how to communicate with a specific device is
A. Device interface
B. Device driver
C. Console program
D. Server OS
ANSWER: B
108. In computer memory, the word “girl” is represented as how many bits?
A. 4
B. 8
C. 16
D. 32
ANSWER: C
SECTION B
FILL IN THE BLANK SPACES
i) The ASCII is the abbreviation of ………………………………………………………..
ANSWER: American Standard Code for Information Interchange
ii) A paragraph is a ………………………………………………… bit data item
ANSWER: 128
iii) Unsigned numbering system is made up of ………………………………………………..
ANSWER: Binary
iv) Bank Teller can be likened to the ……………………………………… Mode in the OS
ANSWER: Kernel
v) The most important schema in data abstraction is the ………………………………….
ANSWER: View level
vi) The …………………………………….. is normally termed as the brain of the computer
ANSWER: Central Process Unit (CPU)
vii) A student and a course is a typical example of …………………………………. Relationship in an ER Diagram.
ANSWER: Entity Relationship
viii) Concurrency Access goes with ……………………………… recovery in DBMS
ANSWER: Crash
Vx) The 2000s in the history of Database systems was relevant to ……………………………..
ANSWER: Internet Technology
ix) PCI slot on the motherboard is the abbreviation of………………………………….
ANSWER: Peripheral Component Interconnect
SECTION C
i) a) Use DIAGRAM ONLY to differentiate between Ring Topology, Star Topology and Mesh Topology.
b) Convert 9DE16 to Binary
c) Convert 15010 to Hexadecimal
ANSWER:
a)
| |
Answer:
9 D E 1 6
9DE16 = 1001 1101 1110 0001 0110
c)
Answer:
c) Convert 15010 to Hexadecimal
16 15010 R
16 938 2
16 58 10
16 3 10
3
3,10,10,2 = 3AA2
15010 = 3AA216
Notice;
Explanation on C,
15010/16 = 938, Remainder 2
938/16 = 58, Remainder 10
58/16 = 3, Remainder 10
3/16, can't be,. So Remainder 3.
3/16, Since 16 can't divide 3, we bring the 3 at the down of the Remainders and now start to arrange from bottom to up, which will be 3, 10, 10, 2. In hex 10 is A, so replace all the 10s with A, and you will get 3AA2 with the base 16 written beside it.
i) a) Use DIAGRAM ONLY to differentiate between a Client-Server and Peer- to -Peer Network
ANSWER:
b) Use DIAGRAM ONLY to illustrate the Von Neumann Architecture
SECTION D
What is a computer software?
ANSWER:
Computer software is programming code executed on a computer processor.
Differentiate between System and Application Software (Give two examples of each)
ANSWER:
System software are general-purpose software primarily used to operate a system with computer hardware. Eg. Apple macOS, Microsoft Windows, Google's Android OS, Linux Operating System, and Apple iOS
Application software are specific-purpose software primarily used to perform certain tasks. Eg. Ms Word, Ms Excel, Web browser, Media player etc.
What is an operating System?
ANSWER:
An operating system (OS) is system software that manages computer hardware, software resources, and provides common services for computer programs.
List four major function of an operating system
ANSWER:
· Processor Management
· Memory management
· File management
· Device Management
· Security
Define a computer Network
ANSWER:
It two or more computer device link together my the same form of transmission medium, such as cable, wireless, to share resources or file.
List the four major classification of computer Networks
ANSWER:
· LAN(Local Area Network)
· PAN(Personal Area Network)
· MAN(Metropolitan Area Network)
· WAN(Wide Area Network)
Differentiate between LAN, WAN and MAN
ANSWER:
LAN is defined as a computer network that links the local areas like schools, universities, organizations, etc.
On the other hand, MAN is defined as a computer network that links the metropolitan areas.
On the other hand, WAN is defined as the telecommunications network that covers a large geographical area.
Which kind of network Topology is adopted by Banks?
ANSWER:
Mesh Topology
Differentiate between internet and world wide web.
ANSWER:
The Internet is a global system of computer networks interconnected through telecommunications and optical networking.
In contrast, the World Wide Web is a global collection of documents and other resources, linked by hyperlinks and URIs.
Differentiate between a Database and a Database Management system.
ANSWER:
Database is a collection of interrelated data. Database management system is a software which can be used to manage the data by storing it on to the data base and by retrieving it from the data base. And DBMS is a collection of interrelated data and some set of programs to access the data.
List four major advantages of DBMS
ANSWER:
· Physical Data independence
· Logical Data independence
· Data Integrity & Privacy
· Reduction of Redundancy
· Concurrent Access
· Easy Recovery, Crash Recovery
· Efficient Data Access
What is Database Abstraction
ANSWER:
It is the Process of hiding irrelevant details from the user.
With the aid of a diagram explain the levels of abstraction in a database system
ANSWER:
Differentiate between DML and DDL
ANSWER:
· DDL stands for Data Definition Language. DML stands for Data Manipulation Language.
· DDL statements are used to create database, schema, constraints, users, tables etc. DML statement is used to insert, update or delete the records.
SECTION E
A Biometric inputs are ways to input data into computer system, Mention three (3) biometric technologies that you know and explain their use.
State and describe, three input devices for physically challenge people
· Braille keyboard and Braille display device: These are keyboards with Braille lettering, that can be used by blind or visually impaired users.
· On-screen or virtual keyboards: The keyboard is displayed on a user’s screen and used with gesture-controlled pointers or joysticks.
· Microphones: Are used with speech recognition software, allowing the user to dictate their input to the computer.
· Keyguards: Metal or plastic plates that allow a user to rest his/her hands on a keyboard without accidentally pressing the keys.
· Head-mounted pointers: These are controlled by switches to simulate the function of a mouse. The switches can be in hand or foot pads, or pedals or sensors that detect eye movement or facial expressions.
· Gesture-recognition devices: The device recognises hand gestures, head or eye movements, or read lips or sign language to input information into a computer.
· Sip-and-puff devices: A switch that operates the computer when users breathe into (puffing) or through (sipping) special tubes. Special software is used to interpret the sips and puffs and turn them into data that the computer can use.
· Magnification devices: Enlarges the information displayed on the computer screen in a range of magnifications and a variety of fonts. The magnifier may have the ability to create a large, scrolling virtual screen, or may only magnify the portion of the display near the mouse pointer.
· Large-key keyboards: The print on the number and letter keys of the keyboard are three times larger than those on standard keyboards. The bright white printing on the large black keys increases visibility and the contrast makes it easier to read. These features are helpful to those with vision impairment and for those who wear reading glasses or bifocals, or work in low-lit areas.
· Braille printers: These printers operate by embossing raised braille dots onto Braille paper. Pins are pressed into one side of the paper in order to create raised dots on the other side. This is only output.
Thanks for checking out our questions and answers in this blog! I hope the information was helpful. Please let us know in the comments section below if you have anything to add or think I missed something important. As always, feel free to share this post’s link on your social networks and never forget to appreciate and Like our Facebook other media Pages!
If you have any questions, then you should join our Telegram chat group. We will help you solve your problems with blogging and SEO.